I Let Myself Get Hacked
I let myself get hacked, and here's what I learned...
Ok, clickbait-y opener aside, I wanted to practice some DNS skills and learn more about web scrapers and bot accounts. I bought a cheap domain name, and spun up a server using DigitalOcean. Using Joda32's Outlook Honeypot, I hosted a fake Outlook login page, and I waited...
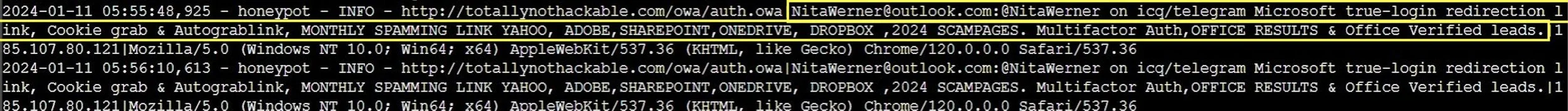
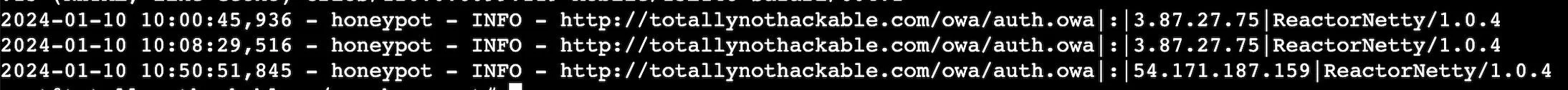
Within 24 hours, I received multiple logon attempts from a Netty application, more than likely a web scraper. Within another day or two, I received login attempts from someone trying to sell their phishing services. Overall, there was more than a dozen attempts.
While I would've loved this experiment to continue, my domain registrar shut down the domain due to "suspected phishing"- which I suppose IS valid!
The lesson? As soon as something is exposed to the internet, it will immediately be a target for bots. Attackers don't need to be looking through everything manually- instead, bots can do most of the legwork, allowing them to expand their reach and search for exposed assets. Always double check who can access your org's resources! Anything exposed to the internet is in danger of being targeted. I know this isn't groundbreaking news, but it is crazy to watch happen in real time. Stay safe and secure!
Disclaimer: The opinions and content are my own and do not necessarily represent Edgile’s position or opinion.